Fuzzing Android: A Recipe For Uncovering Vulnerabilities Inside System Components In Android
❤ 605 , Категория: Новости, ⚑ 15 Авг 2017г
by Alexandru Blanda
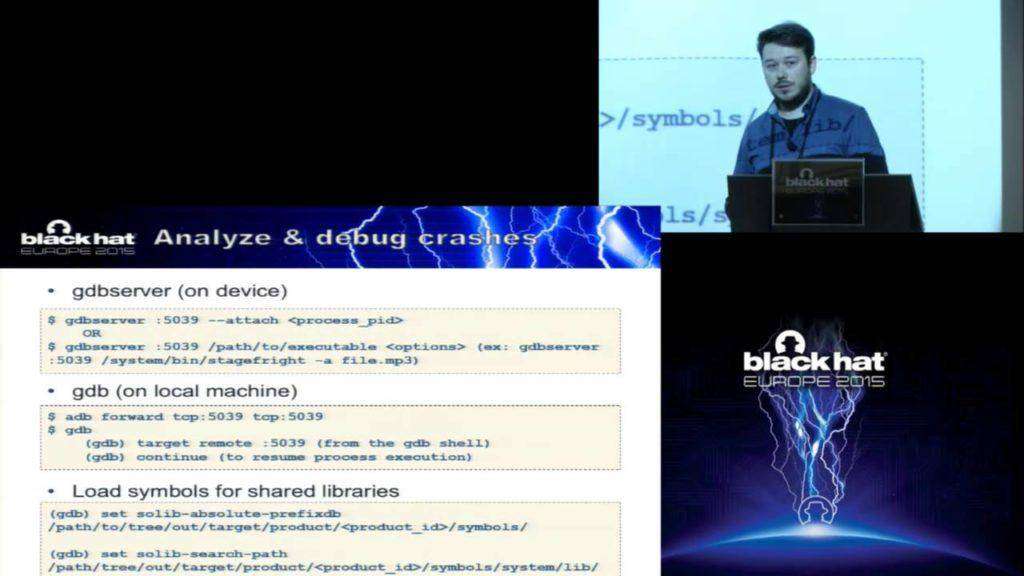
The presentation focuses on a fuzzing approach that can be used to uncover different types of vulnerabilities inside multiple core system components of the Android OS. The session will be targeted on exposing the general idea behind this approach and how it applies to several real-life targets from the Android OS with examples of actual discovered vulnerabilities. Some of the components that were targeted and found vulnerable: the Stagefright framework, the mediaserver process, the Android APK install process, the installd daemon, dex2oat, ART.
The presentation will cover a number of topics starting with the actual fuzzing process with the data/seed generation processes and test case execution, the logging and triage mechanisms, addressing challenges such as bug reproducibility, sorting out unique issues and prioritizing issues based on their severity. The second part of the presentation will take the talk towards explaining the creation of several tools that have been developed using this methodology. The actual implementation of the tools will be discussed with focus on the more innovative technical details, as well as the issues discovered, CVE entries released and possible exploitable patterns. An insight of the results that will be discussed: thousands of crashes discovered, tens of unique issues, 6 CVE entries released by Google.
Источник
Похожие записи